Table Of Content
Calling a method from another machine is then made possible simply by calling a method of the proxy object. Any call to proxy object is used for additional requirements and the call is passed to real object. A proxy object hides the original object and control access to it. We can use proxy when we may want to use a class that can perform as an interface to something else. Overusing the Proxy object or performing heavy operations on each handler method invocation can easily affect the performance of your application negatively.
Relations with Other Patterns
This will allow our proxy to be used wherever a ReportGeneratorImpl object is expected. In Line 5, we declared a reference to the ReportGeneratorImpl object. By going with the principle of “Prefer composition over inheritance”, we me made our proxy composed of the real ReportGeneratorImpl object.
Subject (Image Interface):
We will delve deep into the concepts, principles, and real-world applications of the Proxy pattern. Instead of creating the object when the app launches, you can delay the object’s initialization to a time when it’s really needed. This example illustrates how the Proxy pattern can help to introduce lazy initialization and caching to a 3rd-party YouTube integration library. You need to support resource-hungry objects, and you do notwant to instantiate such objects unless and until they are actuallyrequested by the client. Proxy is invaluable when you have to add some additional behaviors to a class which code you can’t change.
Performance Patterns
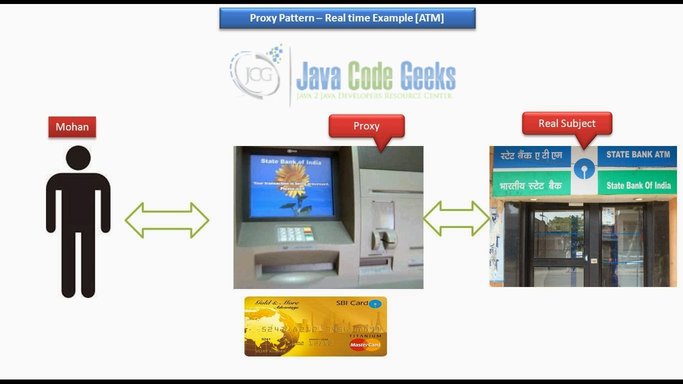
So, here, the Bank is the Real Object, and the ATM is the Proxy. And I think this is the best Real-Time Example of the Proxy Design Pattern. Tutorials Point is a leading Ed Tech company striving to provide the best learning material on technical and non-technical subjects. Use the ProxyImage to get object of RealImage class when required.
Key Concepts of Proxy Method Design Pattern in Java
This pattern can be particularly useful in situations where you need to add an extra layer of control, lazy loading, or remote access to objects. Proxy is a structural design pattern that provides an object that acts as a substitute for a real service object used by a client. A proxy receives client requests, does some work (access control, caching, etc.) and then passes the request to a service object.
For example, a company might use a Proxy Server to prevent its employees from accessing a specific set of websites such as Facebook, Twitter, etc. Please look at the following diagram to better understand the Proxy Design Pattern. On the right-hand side, you can see the State Bank of India; on the left, you can see a person called Anurag. In earlier days, let’s say 1980, Anurag wanted to withdraw money from his account. Once his turn comes, he has to give the form and bank passbook to the bank employee, and then the bank employee verifies the form and his passbook.
Efficient and robust optimization for well patterns using a PSO algorithm with a CNN-based proxy model - ScienceDirect.com
Efficient and robust optimization for well patterns using a PSO algorithm with a CNN-based proxy model.
Posted: Sun, 13 Jun 2021 05:56:26 GMT [source]
Virtual Proxies wrap expensive objects and loads them on-demand. Sometimes we don't immediately need all functionalities that an object offers, especially if it is memory/time-consuming. Calling objects only when needed might increase performance quite a bit, as we'll see in the example below. As its name suggests, the proxy pattern means using a proxy for some other entity. In other words, a proxy is used as an intermediary in front of, or wrapped around, an existing object. This can be used, for example, when the actual object is very resource-intensive or when there are certain conditions which need to be checked before using the actual object.
The Proxy Design Pattern: Mastering Controlled Access to Objects
For example, two users, X and Y, want to access a particular resource through the Proxy Server. First, user X requests a particular resource (a list of employees), and the Proxy Server gets the data from the real server. Before sending the data to the client, it caches that resource (list of employees) for some time. You may have observed that many patterns in the GoF structural family are about “wrapping” a class, but with variations.
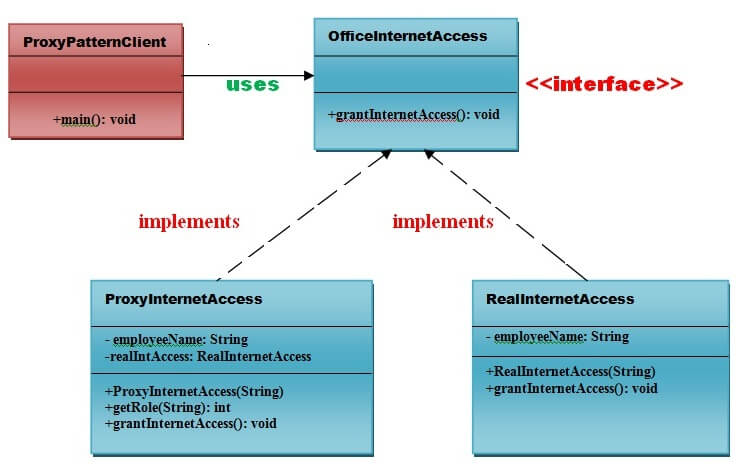
We allowed access to the ReportGeneratorImpl object only if the role name is Manager. The pattern involves creating a new class (the proxy) that acts as an intermediary or placeholder for an object (the subject) to control access to it. The proxy can be a local representative of the subject, which helps in various tasks such as lazy initialization, access control, logging, monitoring, or remote communication. Design Patterns are an essential part of software engineering, offering proven solutions to common problems encountered during software development. The Proxy Pattern is a structural design pattern that provides a surrogate or placeholder for another object, allowing you to control access to it.
A protection proxy might be used to control access to a resource based on access rights. When accessing sensitive objects, for example, it should be possible to check that clients have the needed access rights. It also implements the Image interface, maintaining a reference to the real image object.
Here, we have declared one method called PerformRWOperations, which both Real Object and Proxy Object will implement. Please look at the following diagram to understand the Proxy Design Pattern in C#. As you can see in the following image, when the client wants to consume some methods of the Real Object, he/she needs to go via the Proxy object. That means the client will call the method of the Proxy object, and the proxy will be responsible for calling the method of the Real Object.

No comments:
Post a Comment